This article is in response to all the requests I have seen on Facebook, asking how to easily calculate the radius of a curved Lithophane created using http://3dp.rocks/lithophane/. This information can then be used to create custom enclosures. My first attempts at making this calculation consisted of printing the curved Litho and then measuring the straight-line distance between the two curved ends, called a chord. Because I was creating Litho’s with a ninety-degree angle is simplified the calculation greatly, since the chord became the hypotonus of an equilateral right triangle. The radius equals the chord divided the square root of two. If I had chosen any other angle I would have had to measure both the chord and the distance between the chord and the highest point on the arc. I would then plug the numbers into a slightly more complicated formula that you can lookup on Google if you want to know more about it.
There is a problem with this method of calculating the radius, you must print the curved litho before designing the enclosure. Plus making accurate measurements can be a pain in the proverbial butt. After much though I believe I have figured out a way to calculate the necessary information to create the enclosure without printing the Litho first.
When creating a custom enclosure for your curved Lithophane you need to calculate the unknown dimension of the Litho and its radius. The unknown dimension represents the length of the shorter side of the Litho image in millimeters. The longer side is set by the Maximum Size option in 3dp.rocks Litho model settings. These settings can be calculated in three steps.
Step 1. XnView
The first step is to download and install a program like XnView. XnView is an application that I have been using for many years to read, view and process images. It is available for Windows, Linux, and OSX.
This program will provide the necessary physical dimensions in centimeters or millimeters of the original image that is being used to create the Litho, depending on the version of XNView installed
- Open the image that you are going to convert to a Lithophane.
- Select the View -> Resize menu
- Under Print size change the measurement to cm or mm.
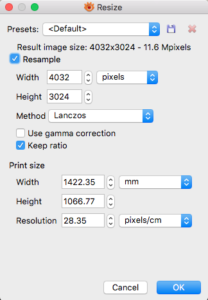
- Record the Print size Width and Height values to be used in your calculations.
- If the measurements given are in cm then multiply each number by 10.
Step 2. Determine the new dimensions of a Lithophane created in 3dp.rocks
Original Ratio Calculation:
![]()
Use the appropriate formula depending on the shape of your image. Remember that the Maximum Size setting determines the length of the longest side of the image.
- New Width = (Orig Width * New Height) / Orig Height
- New Height = (New Width * Orig Height) / Orig Width
Example:
Using the example numbers in the above XnView image we can calculate the new heights of the Litho if the Maximum Size is set to 100mm.
New Height = (100 * 1066.77) / 1422.35 = 75.00 mm
Step 3. Determining the Radius of the curved Litho
Two values from 3dp.rocks are needed to make the radius calculation. Maximum size and Angle value. Plug the values into the formula below to calculate the needed radius.
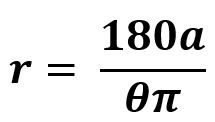
r = Radius of arc
a = Length of arc (Maximum Size value from 3dp.rocks or calculated width)
θ = Angle of arc (Curve value from 3dp.rocks)
π = pi (3.14159)
Examples:
Using the same Maximum Size value, the radius can be calculated any size radius.
60 degrees -> r = (180 * 100) / (60 * 3.14159) = 18000/188.4954 = 95.49 mm
90 degrees -> r = (180 * 100) / (90 * 3.14159) = 18000/282.7431 = 63.66 mm
Real World Considerations
Due to the dimensional inaccuracy that can plaque 3D prints there might be slight a variance in the printed size and therefor radius of the Litho when compared to the calculations. When comparing the measurements from my existing printed curved Lithos to my calculations I found up to a two mm increase in the printed width and height. This may be due to printer calibration and/or filament type. I am using eSun white PLA on an Original PRUSA MK2S. I also suspect the size and shape of the printed Litho will also determine the size of the variance. I measured a few of my smaller flat Lithos and the calculations were nearly perfect. I have not yet printed a curved Litho under 200mm so far so have not tested this theory in that scenario.
I want to warn everyone that my math skills are very rusty so if I have made any mistakes or there is a simpler way to accomplish this task please let me know. This process came to me in a moment of inspiration and appears to work better than I expected. Hopefully it also works for you.



